click here to enlarge
(.pdf)
 Download
DDV-3000™ datasheet (.pdf) Download
DDV-3000™ datasheet (.pdf)
DDV-3000™
Topologies
Due to DDV-3000™unique modular architecture, various customizations,
including topologies are easily possible. To facilitate use, increase
overall storage capacity or due to simple physical constraints,
DDV-3000™ can easily adapt. Here are some possibilities:
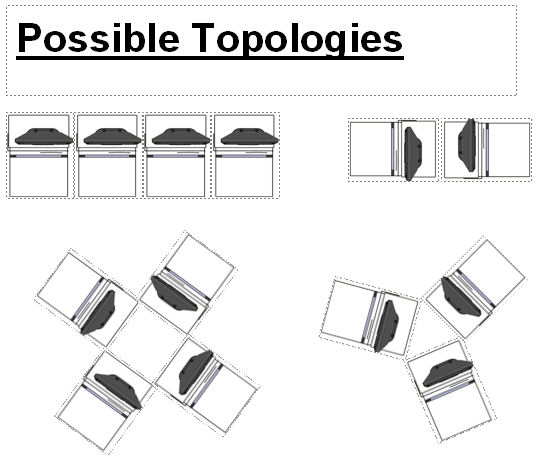
In addition, any number of machines can be daisy-chained as needed
to increase the overall capacity as needed.
 Download
DDV-3000™ datasheet (.pdf) Download
DDV-3000™ datasheet (.pdf)
|
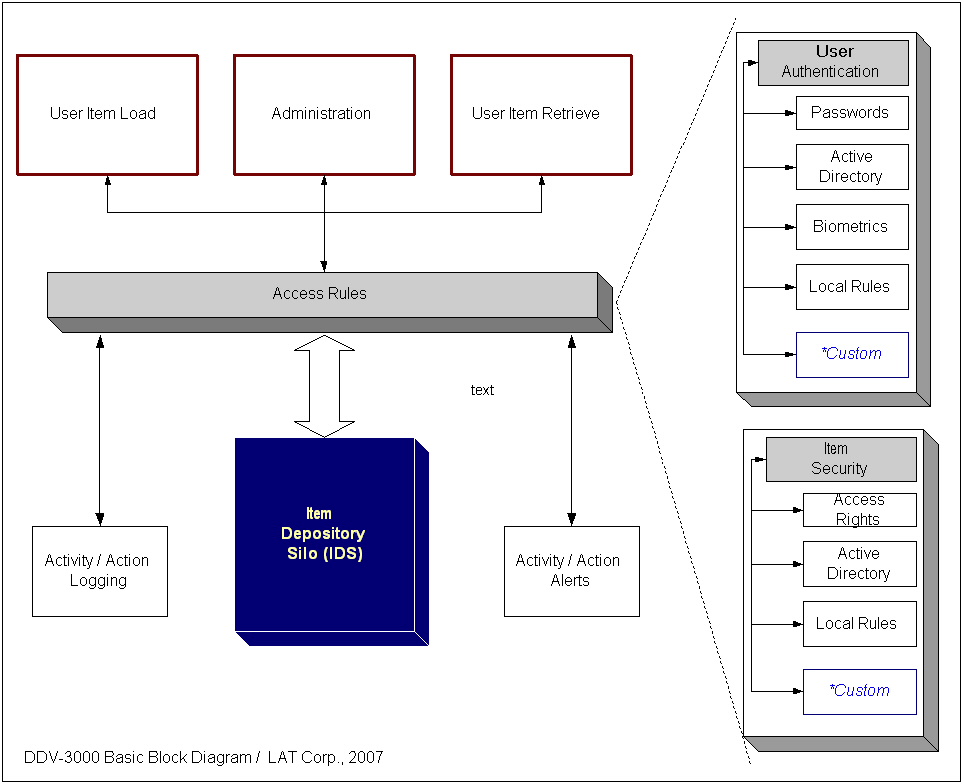
50,000 foot view...
The "DDV-3000" allows complete physical protection
of your CD/DVD/Blu-Ray/HD - based media. Access control is protected
by conditions and rules that you specify. All
activity is logged and automated alerts are issued if any of the
predefined conditions are met.
A bit closer ...
Refer to the picture on the left.
All of the user actions are governed by the "access rules"
layer as depicted in the diagram. Whether the user wants to load
an item into the DDV-3000™ or retrieve an item from DDV-3000™
- all of these actions and more are controlled by the rules.
When and if the rules allow the transaction to proceed, all of
the items are ultimately wound up in the Item Depository Silo
or IDS. The IDS is essentially an automated, steel protected "vault"
that safely houses all of the physical items that DDV-3000™
is responsible for.
Any transactions that are performed on the system, even if they
are not successful, are completely logged in internal logs and
databases. These logs serve as a detailed "trail" that
allows post-action analysis and control.
In addition to detailed logging, detailed alerts can be setup.
These alerts can generate a number of "actions" that
DDV-3000™ can initiate based on specific criteria. The "actions" that can be generated can
be easily expanded and customized to fir your specific needs.
Here is some more detailed information on key components of the
rules layer:
User Authentication
Looking at the right of the diagram, is a "blow-up"
view of the "access rules" layer. As you can see, before
anything can happen, the user must be authenticated to the DDV-3000™.
This authentication can take on many forms. It can be as simple
as a predefined password, something that is based on your existing
network credentials, or as complex as biometric verifications.
Any combination is possible as well. LAT will work with you to
determine the best possible level of authentication required and
pre-configure
DDV-3000™ to that standard.
Item Security
Similar to user authentication, item security has its own subset
of rules and conditions that guarantee its integrity. The rules
that apply to physical items are completely separate from the
user rules. That is, a "high" rights user may still
not be able to reach "sensitive" data elements stored
in IDS. The item-level rules can be defined and controlled in
a number of ways, largely based on your corporate policies and
document management processes. Suffice it to say that DDV-3000™
can easily support a number of options where the item rules can
be specified.
 Download
DDV-3000™ datasheet (.pdf) Download
DDV-3000™ datasheet (.pdf)

|